Borders between real and virtual no longer exists. Someone understands that it’s a fact, someone is trying to deny it, but intuitively feels that already drawn into this discourse ... The rest, like Robinson Crusoe, stuck on a desert island and the world does not know about their existence. IN Anyway, with the development of the Internet and the technological boom, we got additional reality, which gradually ceased to be considered additional and became our lives with you.
and these lives are ordered by laws and obey rules so as not to slide into the chaos of anarchy. But with any device of society are people who violate these rules, as well as those who try them stop. Equally ordinary users, business owners or corporations suffer from scammers, hackers, extremists and government and special services opposing them.
Since cybercrime is based on the theft of personal data with the aim of using them for personal purposes of the offender. It is worth protecting yourself and get a healthy level of paranoia, prepare your devices and conduct educational program for friends and colleagues, since the success of such crimes often directly proportional to victim's confidence level or vulnerability software.
Let's start in order. How to prepare your devices?
1.Password

Imagine the safe where your data is located, it is stored securely there. Access to it can only be obtained using a special combination. And from The complexity of this combination depends on the safety of your data. qwerty 123456, 12345678, password - make up a little more than 1% of all passwords world, it’s okay. The remaining 99-98% are more complex, but in mostly made up of repeating semantic kernels, and powers modern hacking software is enough to calculate Most of them. Thus, your safe is at risk and you need to add an alarm and constant monitoring to the castle:
-
Create one complex password or randomly generate one
so that your name, surname, date of birth or
nicknames of a beloved dog. Different registers and
Special symbols. Remember it and use only for trusted
reliable resources, do not use it for entertainment or
questionable portals, for this it is better to make a separate box, which
I’m not sorry to lose.
- Make secret phrases secret. For example, to hack your mail you need to enter the name of your pet. Of course, photos from it is in your profile on social networks, there is also an answer to question.
- If possible, use double authentication, yes it is annoying, but it works fine.
2.Update software

here
everything is simple, but do not bypass this question. Vulnerability in
software provides a loophole through which an attacker can
force the software to perform the action it needs to which it does not have rights. AND
in this way access your personal data. For
To avoid such a fate, the following rules should be observed:
-Put the antivirus and update its database. Every day there are new threats, which are becoming more complex and inventive. Qualitatively a working antivirus helps to cope with most known threats and take care of your nerves.
-Update applications. if you are using outdated versions of email clients, browsers or applications for social networks, their likelihood is growing hacking. You can avoid these problems by setting up automatic updates.
-Update operating systems. This “double-edged sword”, on the one hand the threat level here is higher than in browsers and office applications therefore a system update is needed. On the other, updating the OS to a new “Raw” version, may produce unpredictable results. Not worth it in a hurry, it’s better to wait until the system is brought to mind, and only after this is boldly updated.
3. Turn off geolocation

Collection further processing and analysis of data helps make Google and Apple Ads are more targeted and ultimately less intrusive. Same The function helps to monitor the weather, the route traveled and find out where are your loved ones and in real time monitor traffic jams all this a plus. The downside is that your personal data is collected without your knowledge and can be used for personal gain by corporations, and so same scammers. Therefore, if you do not completely disable this function, then include it only when necessary. For example, when searching for a route or photos with friends. It will also have a positive effect on time. work of your smartphone.
4. We use encrypted messengers.
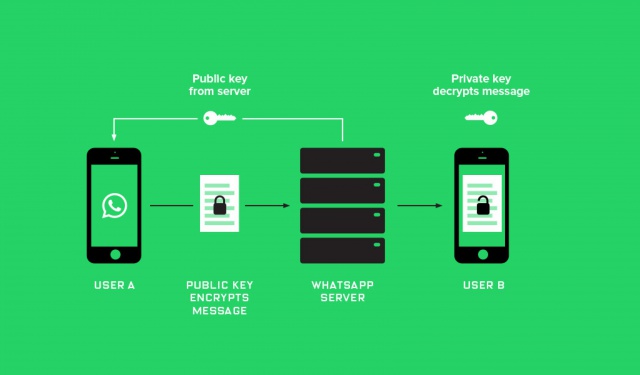
no theories of surveillance and conspiracy, but everything you do on the Internet can be used against you. There have been a lot of resonance in the media lately news about someone being planted for reposts and comments online. All data about yourself in social. networks are provided voluntarily and by it’s quite easy for them to compose a psychological portrait of the user his needs. If you want more privacy then it’s worth transfer communication from social networks to instant messengers like Viber or Telegram
5. Is it worth sticking a webcam and microphone?

Actually yes, since hacking the camera your laptop is easy for hackers, as well as access to Your camera may receive special services. e.g. creator of social Facebook Zuckerberg and other famous personalities also support this initiative.
Summary:
Today
we talked about how to secure our devices and thereby increase
the security of your personal data. In the next publication, we will cover
examples on how to behave correctly on the Internet so that
prevent data leakage.
In order not to miss the publication, subscribe to our blog:
FB: https://www.facebook.com/citysitesglobal/
